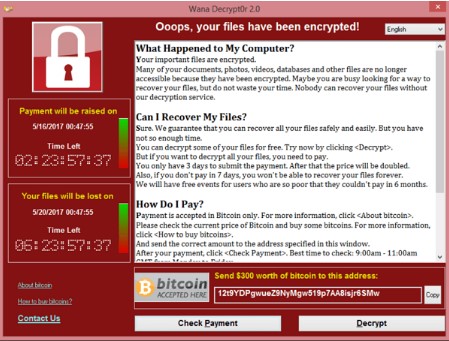
The funny thing about ransomware is that they give them very strange names: Bad Rabbit sounds like the name of a villainous bunny who gets his comeuppance in some type of modern nursery rhyme, not malware that would ravage hundreds of European businesses. Locky seems like the son of Candado de seguridad, a character Medeco would come up with to educate kids on proper physical security. The latest in a long line of funny-named ransomware, SamSam, isn’t a pet name for your pet ferret you perplexingly named Sam, it is one of the worst ransomware strains ever, and it has caught the attention of U.S. Federal law enforcement.
Both the Federal Bureau of Investigation and the Department of Homeland Security have issued alerts for the ransomware, also known as MSIL/Samas.A. The alert was issued on December 3, 2018, and outlines an attack on multiple industries, some with crucial infrastructure. The ransomware has been in the news as of late, as two Iranian nationals, Faramarz Shahi Savandi and Mohammad Mehdi Shah Mansouri were indicted by a U.S. grand jury in New Jersey for ransomware attacks on the Colorado Department of Transportation.
The pair is alleged to have victimized over 200 hospitals, businesses, government agencies, and schools in the U.S. and Canada beginning in 2015; extorting over $6 million over that time. In addition to these charges, the two hackers have now been indicted by the state of Georgia on charges that they were the ones that perpetrated the ransomware systems that crippled Atlanta’s government in March of 2018. By taking almost 3,800 of the City of Atlanta’s computers hostage, prosecutors state that Mansouri and Savandi have cost the city millions of dollars in consultant fees, downtime, and other costs.
What is SamSam?
SamSam is a privately developed ransomware that is being used to target specific companies selected by the developers. This means that it isn’t just a commodity ransomware, it can’t be found on some type of criminal forum on the dark web, and it isn’t sold as a service like many other forms of ransomware. This is a major problem for any organization that is targeted, as none of the typical endpoint defensive strategies work to stop it.
What’s worse, is that that once a SamSam strain is used, and security vendors publish a report, another SamSam strain is developed. It is thought that this development team includes the two hackers implicated in the Colorado DoT crimes, the Atlanta crimes, and hundreds of other attacks over the past three years.
What Can You Do?
Thus far the SamSam ransomware has entered victims’ networks using exploits in web-facing servers. It has been deployed as millions of other pieces of malware as an executable file that is mistakenly unleashed, or via brute force via the Remote Desktop Protocol. So, while you can lock down your RDP, your best bet is to have a dedicated strategy that:
- Doesn’t allow unauthorized users to have administrative privileges
- Limits use of Domain Access accounts to administration tasks
- Doesn’t provide service accounts for important services
- Restricts access to critical systems
If you are diligent in your organizational cybersecurity practices, you should be able to conduct business as usual without having to worry about ransomware, SamSam or otherwise. If you are interested in knowing more about SamSam and how to stop it, contact the IT professionals at The Connection, Inc for more information at (732) 291-5938.